A computer network is an interconnection of a group of computers. Networks may be classified by what is called the network layer at which they operate according to basic reference models considered as standards in the industry such as the four-layer Internet Protocol Suite model. While the seven-layer Open Systems Interconnection (OSI) reference model is better known in academia, the majority of networks use the Internet Protocol Suite (IP) as their network model.
By scale:
Computer networks may be classified according to the scale: Personal area network (PAN), Local Area Network (LAN), Campus Area Network (CAN), Metropolitan area network (MAN), or Wide area network (WAN). As Ethernet increasingly is the standard interface to networks, these distinctions are more important to the network administrator than the end user. Network administrators may have to tune the network, based on delay that derives from distance, to achieve the desired Quality of Service (QoS). The primary difference in the networks is the size.
Controller Area Networks are a special niche, as in control of a vehicle's engine, a boat's electronics, or a set of factory robots
By connection method
Computer networks can also be classified according to the hardware technology that is used to connect the individual devices in the network such as Optical fiber, Ethernet, Wireless LAN, HomePNA, or Power line communication.
Ethernets use physical wiring to connect devices. Often, they employ the use of hubs, switches, bridges, and routers.
Wireless LAN technology is built to connect devices without wiring. These devices use a radio frequency to connect.
By functional relationship (Network Architectures)
Computer networks may be classified according to the functional relationships which exist between the elements of the network, e.g., Active Networking, Client-server and Peer-to-peer (workgroup) architectures.
By network topology
Main article: Network Topology
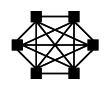
Computer networks may be classified according to the network topology upon which the network is based, such as Bus network, Star network, Ring network, Mesh network, Star-bus network, Tree or Hierarchical topology network, etc.
Network Topology signifies the way in which intelligent devices in the network see their logical relations to one another. The use of the term "logical" here is significant. That is, network topology is independent of the "physical" layout of the network. Even if networked computers are physically placed in a linear arrangement, if they are connected via a hub, the network has a Star topology, rather than a Bus Topology. In this regard the visual and operational characteristics of a network are distinct; the logical network topology is not necessarily the same as the physical layout.
By protocol
Computer networks may be classified according to the communications protocol that is being used on the network. See the articles on List of network protocol stacks and List of network protocols for more information. For a development of the foundations of protocol design see Srikant 2004 [1] and Meyn 2007